Blog & Tools
-
 For network building team, 2017 will be the year of small cell poles
For network building team, 2017 will be the year of small cell poles -
 3 Easy steps to stay off 2017's Worst Password list
3 Easy steps to stay off 2017's Worst Password list -
 Theron McChesney’s research helps SDN and its customers
Theron McChesney’s research helps SDN and its customers -
 SDN network architect Gary Glissendorf is a self-taught expert
SDN network architect Gary Glissendorf is a self-taught expert -
 Thune, Klobuchar want all calls to connect (Update)
Thune, Klobuchar want all calls to connect (Update) -
 SDN’s Jake VanDewater helps businesses fight cyber threats
SDN’s Jake VanDewater helps businesses fight cyber threats -
 Cyberattacks can come from anywhere, even school kids
Cyberattacks can come from anywhere, even school kids -
 Immunity from hacking has not been granted to law firms
Immunity from hacking has not been granted to law firms -
 Experienced telecom executive joins SDN team in Minnesota
Experienced telecom executive joins SDN team in Minnesota -
 Small cell technology helping improve wireless services
Small cell technology helping improve wireless services -
 Tips from FBI to prevent and discourage ransomware attacks
Tips from FBI to prevent and discourage ransomware attacks -
 Golden West celebrates 100 years and keeps looking ahead
Golden West celebrates 100 years and keeps looking ahead -
 Surprise! Your company’s network probably has been breached
Surprise! Your company’s network probably has been breached -
 Seven tips to help protect your business from email scams
Seven tips to help protect your business from email scams -
 More businesses should consider encrypting sensitive data
More businesses should consider encrypting sensitive data -
 Businesses should take note of consumers’ privacy concerns
Businesses should take note of consumers’ privacy concerns -
 Security experts offer advice to help businesses protect data
Security experts offer advice to help businesses protect data -
 Oops, you clicked on a bad link. What should you do now?
Oops, you clicked on a bad link. What should you do now? -
 Hackers zeroing in on data-rich health care industry
Hackers zeroing in on data-rich health care industry -
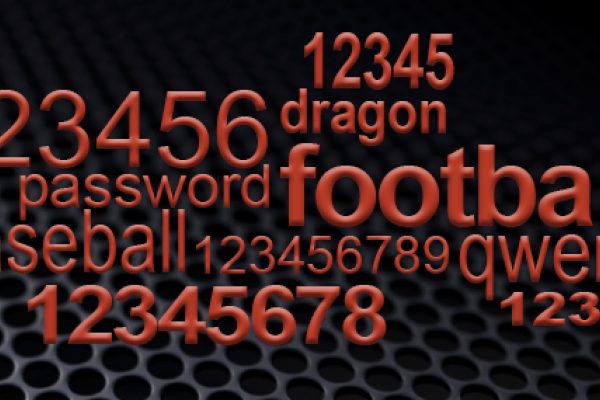 Passwords: A recipe for security, words to avoid
Passwords: A recipe for security, words to avoid