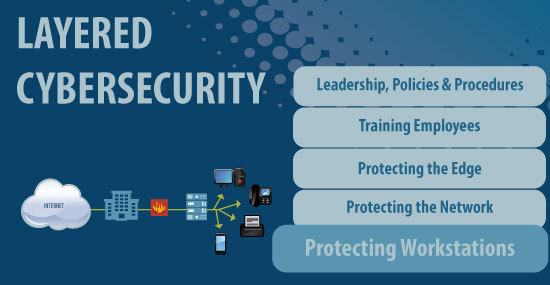
Deploying an effectively layered cyber defense means that every point of access in an organization’s network must be strongly protected. That includes workstations. All of them.
Regardless of whether employees are working from a desktop computer in an office, a laptop in a coffee shop or a mobile phone from a car, good procedural and mechanical protections must be in place to adequately protect the organization’s electronic assets.
Cyber criminals are using an evolving array or electronic weapons and constantly are looking for mechanical or human vulnerabilities. No level of an organization’s network is immune from danger.
“Every level matters, whether it’s the PC or the network,” says Chad Pew, manager of IT for Sioux Falls-based SDN Communications. “Your security is as strong as the weakest link.”
Protecting workstations is a largely human element that requires informed planning, up-to-date hardware and software, and a lot of common sense.
Workstation protection should begin with good, ongoing training and testing of every employee in an organization. Employees should be trained, for example, to not click on suspicious links or give out sensitive information on the telephone. They should remember to lock doors that are supposed to be locked, and to report suspicious activity.
That might seem elementary, but the vast majority of data breaches in the United States are the result of human error, not equipment failure. That reality attests to the need for better training.
Pew and Tammy Grinnell, who is the supervisor of corporate IT at SDN, and other industry experts offer a number of other suggestions to help keep workstations safe. Among them:
- Workers should use strong passwords. Passwords should include a mix of uppercase and lowercase letters, symbols and numbers, and they should be changed often.
- Regardless of whether it’s the responsibility of the IT staff or individual employees, desktop computers and other connected devices must stay current with security updates. Antivirus, patches and other protective software should be run regularly, and periodic scans should be conducted. The sooner updates can be applied, the better.
- Unapproved software should never be installed. USB drives and other external devices should always be used with caution. Scan content in advance, if possible, and never store sensitive information in easily removed storage devices.
- Limit access to computers with sensitive information and limit who has administrative privileges to groups of users. Security settings on computers should not be altered by individual users.
- Use encryption to protect data whenever possible. It’s especially important to protect data being transmitted on mobile devices such as laptops, which also are at risk because they can be can be lost or stolen.
- Employees should not conduct business on open, unsecured networks in public settings. Meanwhile, organizations trying to protect their data should separate corporate and guest networks. Networks with sensitive information can be physically segregated, or “air gapped” to prevent external connections.
- Backup information. Data should be duplicated and stored in a secure, off-site data center or through a reputable cloud service. This protects the company in case, for example, hackers infect files with ransomware.
Many protective steps are a matter of common sense. If, for example, someone receives an email that appears to be from a delivery service but they’re not expecting a delivery, the person shouldn’t click on any link about the purported delivery, Grinnell says.
“Never click on a link if you question whether it’s safe,” she says.
Pew points out that some workstation protections, such as spam filtering, can be applied by an organization’s IT staff or by a hired vendor. Some companies, including SDN, offer managed services especially designed to help small and midsize businesses deploy and maintain good, protective equipment, such as firewalls.
It’s difficult to generalize about the biggest potential threats to workstations because organization staffing, procedures and equipment vary widely. The common denominator is that nearly every connected workstation is under attack and must be protected.
This is the sixth in a series of blogs about taking a layered approach to cybersecurity. Previous blogs in the series are listed below.
Next, we’ll review some key issues in protecting networks and offer additional suggestions for small and midsize organizations. Use the button below to receive it and our future blogs in our weekly email.
Previous blogs in the series:
Good cybersecurity must start at the top - and stay there
Good training is critical to keeping business networks safe
Protecting edge of a network from outside world is a big job