Firewalls have big jobs, and their duties are getting bigger all the time because of the rising frequency and sophistication of attacks.
A firewall is used at the edge of a computing network and is designed to protect an organization from dangerous Internet traffic. Security engineers can program firewalls to block unauthorized traffic at the entry of a network and let other communications pass through to the next checkpoint or to their destination.
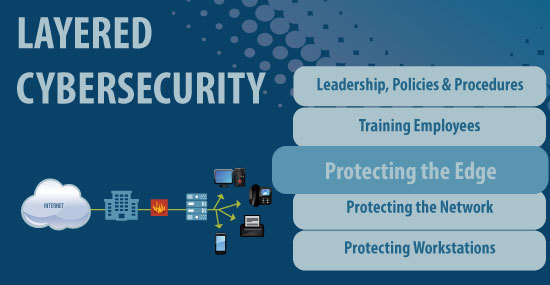
Firewalls typically are the first line of defense in a good, layered cybersecurity system. However, they cannot do the job alone. They need backup help elsewhere in the network.
Firewalls can be hardware, software or a mix of both. The newest class is known as Next Generation Firewalls, which add security functions to standard features.
“Next Generation Firewalls are taking over the market,” says Bill Tetrault, a managed services engineer with SDN Communications in Sioux Falls. “They’re almost required in any regulated business.”
SDN is the leading regional provider of broadband connectivity and cybersecurity services, including Managed Firewalls, for businesses and institutions.
The next step beyond a Next-Generation Firewall is the Internal Segmentation Firewall, which allows for parts of networks to be segmented for additional protection. Segmentation limits the potential for problems in a network to spread, Tetrault says.
“I would recommend it to any business in which security is a priority, which should be every business,” he says.
Switches and routers with more security features also are being developed to help protect networks. Switches and routers are devices that direct and move traffic. But they protect internal networks, not the edge.
Along with Next-Generation Firewalls, Unified Threat Management, or UTM, is a security solution increasingly deployed by organizations to help protect the edges of networks. UTM can include features such as:
- Content filtering
- Spam filtering
- Application controls
- Intrusion Detection (IDS)
- Intrusion Prevention systems (IPS).
UTM also includes the application of anti-virus and anti-malware protection at the edge of networks as well as in the internal network.
Aaron Hansen, a sales engineer at SDN, says maintaining good domain records, such as mechanically listing trusted email addresses, is important for keeping a good safety and corporate reputation.
For example, most cyber threats use a contaminated email to try get an attack past firewalls and into private networks. So it’s natural for companies to closely monitor incoming traffic. Increasingly, companies also are monitoring what leaves their network, Hansen says.
Obviously, companies don’t want employees to send out unnecessary valuable or sensitive information, regardless of whether they’re acting maliciously or a cyber thief has tricked them into cooperating.
Services such as Managed DDoS Protection, which SDN also offers, are another tool to protect the edge of a network. DDoS is short for Distributed Denial of Service. Cybercriminals, pranksters and unscrupulous competitors can and do launch DDoS attacks to overwhelm targeted websites and other online services with malicious, electronic blips. The objective is to block legitimate business traffic or damage equipment.
Managed DDoS Protection services divert attacks before they reach a client’s firewall.
“We take the hit,” Tetrault says. “You keep doing business.”
SDN offers other services that can help businesses and institutions protect the edge of their networks. And will help customers devise and implement an effective strategy regardless of whether some of the tools or services come from other companies. The goal is to keep businesses safe, which requires more than a single layer of protection.
This is the fourth in a series of blogs about taking a layered approach to cybersecurity. Links to the previous blogs are listed below.
Don't stop now. Read the next blog in the series:
Networks must be protected inside the perimeter, too
Previous blogs in the series: