During a workshop in San Francisco earlier this year, there was talk of the need for a new kind of cybersecurity specialist: a ransomware negotiator.
Jeremiah Grossman, chief of security strategy at SentinalOne in California, predicts that insurance companies will employ professional ransomware negotiators in the future.
A ransomware negotiator? Someone to represent business interests in settlement talks with criminals who infect computer systems, lock up files and demand payment to unlock them? Wow. That certainly attests to the growing threat that ransomware presents to businesses.
“Racking up $1 billion in financial losses, 2016 was the year of ransomware,” according to the website DarkReading.com. “In 2016 alone, reports show, almost half of companies in the United States have been hit by ransomware.”
The site also anticipated that 2017 would turn encrypting ransomware with automated targeting into a threat more prevalent than ever.
Not all ransomware attacks are successful, of course. Companies are learning to adequately back up data and to keep their networking equipment and programs up to date. They’re also learning to do a better job training employees to reduce the chances of getting a malware infection by, for example, clicking an infected link in an email.
Related blog: Good training is critical to keeping business networks safe
Related blog: What to do before and after a ransomware attack
However, the black market business remains profitable enough to keep attracting new practitioners.
Small businesses are an increasingly popular target because they sometimes lack the IT staff or equipment to be well protected.
For a variety of reasons, businesses such as medical facilities also have become popular targets.
Enactment of the Affordable Care Act contributed to explosive growth in the creation of electronic medical records that organizations have stored and available for transfer. It’s not clear whether repealing or amending the ACA, as President Trump and some members of Congress want to do, will make patient records more or less vulnerable to attacks.
Regardless, patient records are data-rich targets for hackers and, as a few high-profile national cases have demonstrated, healthcare organizations have shown a willingness to pay ransom rather than lose records.
As of December 2016, more than 15 million people had personal healthcare records, including medical and financial information, compromised in breaches reported to the U.S. Office for Civil Rights.
Related news story: SDN screens Grey's Anatomy episode to learn about cyber attacks
To a large degree, the growing use of ransomware can be attributed to the ease of launching attacks. Criminals don’t have to be technical experts. They can download free software to gain access to the anonymous world of the Dark Web, where do-it-yourself ransomware packages can be secretly purchased with untraceable, cyber currency.
The Dark Web is a flourishing black market cannot be effectively controlled, at least not right now. So the burden falls to businesses to protect themselves. Three basic steps of self-protection include:
- Keep networking equipment and software programs patched and up to date.
- Train employees on an ongoing basis so that they recognize potential threats and are not tricked into exposing business files.
- Regularly back up sensitive and valuable company data on external devices.
Other types of malware, such as Distributed Denial of Service attacks, present significant risks to businesses, too. DDOS attacks are designed to overwhelm targeted computing systems or programs with artificially generated traffic.
DDOS attacks can be more than a temporary inconvenience for businesses. Large attacks can be devastating. But with good protections in place, DDOS attacks can be blocked or at least mitigated.
Ransomware is trickier to stop. The criminals who use it are out to extort money, not just disrupt business. Negotiating with thieves to get a reduced rate for restoring files might be an option. But hopefully the need for professional negotiators won’t materialize to any significant degree.
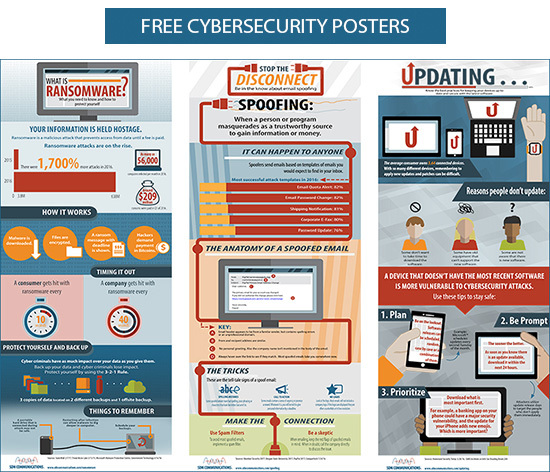
Use the button below to download a trio of cybersecurity posters, including one on ransomware. Print them on legal paper and post them around your company to educate employees.