MANAGED DDOS PROTECTION WITH SDN
Why Your Business Needs Managed DDoS Protection Services
SDN's Managed DDoS Protection service monitors all incoming internet traffic on your network. Our system will prevent the maliciously identified traffic from reaching your network. DDoS attacks can disrupt critical business services such as the internet, email and websites, causing your customers, vendors and employees frustration, time and potential lost revenue.
What is a DDOS attack? How does a DDoS attack work?
Compromised devices participate in an attack, many times unknowingly. They then maliciously distribute (DDoS) robotic armies, or botnets, to attack your network’s digital resources such as computers and servers. When your assets are overwhelmed, the attack cuts off legitimate users, to deny (DDoS) them access to your business and its services, which means lost revenue for you and your clients.
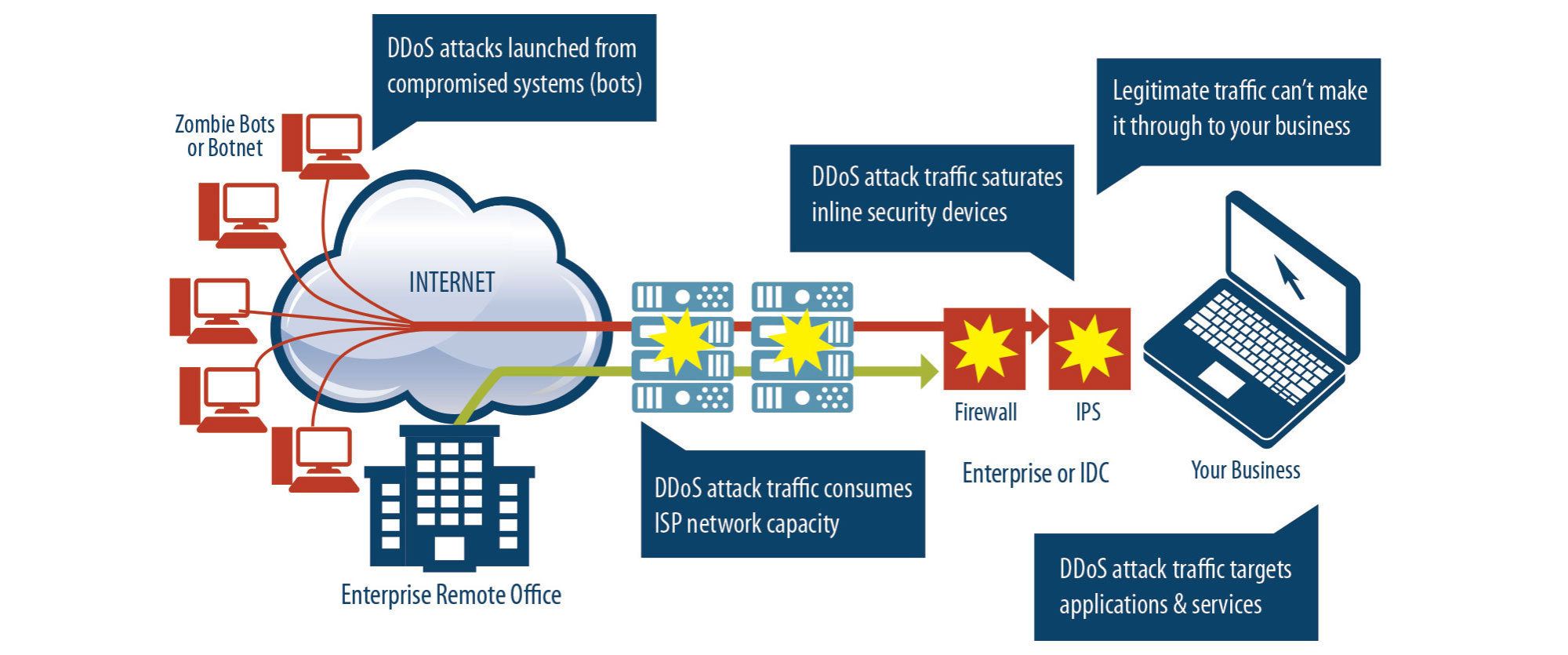
With more business-critical applications moving to the Internet, a DDoS attack can be very disruptive to a business. If you can't afford to be down when a DDoS attack happens, you should pay for the insurance. You may never use it, but if you do use it or need to, you're sure glad you had it.
DDoS attacks are becoming more common. How can you stay protected?
SDN offers multiple levels of protection against a DDoS attack as an additional service to our business internet subscribers. In each package, our Managed DDoS Protection identifies the malicious traffic and has the ability to stop the disruption through mitigation or deploying countermeasures on your internet service. Customers can receive alerts, 24x7 support and scheduled reports, depending on the level of service.
Managed DDoS Protection is a helpful complement to our business internet services, managed firewall services and managed network services. If you depend on the internet to run your business, then you want to make sure your web applications and other services have automatic detection that Managed DDoS Services can provide.
How does SDN’s DDoS protection protect your business?
SDN offers auto mitigation where an attack is stopped automatically with no network technician intervention. The “bad” traffic is rerouted away from the intended destination while legitimate computer requests go through.
The “bad” traffic is rerouted from the intended destination while legitimate computer requests go through. Once the attack stops, all traffic is sent to the customer.
Since legitimate traffic is allowed through while the “bad” traffic is rerouted and discarded, the customer doesn’t know an attack is occurring and can continue with their Internet transactions unaffected.
Managed DDoS Protection Highlights

DDoS Attack Count
Year Over Year
Source: 2021 Year in Review Report

Average Attack Duration
Year Over Year
Source: 2021 Year in Review Report

Average Attack Size
Year Over Year
Source: 2021 Year in Review Report


