Eighty-two percent of social media users say they would consider trying a new product if someone in their network recommended it. Sixty-five percent say they might change their mind on who to vote for if friends in their network supported another candidate.
Findings like those help explain why there are so many automated bots, trolls and fake personas in social media.
Human behavior can be manipulated, and social media is a tool that can be misused to encourage such change.
Twenty-eight percent of online personas are fake, and false accounts and personas drive up to 65 percent of all posts on social media sites, according to social media expert Mary Frantz.
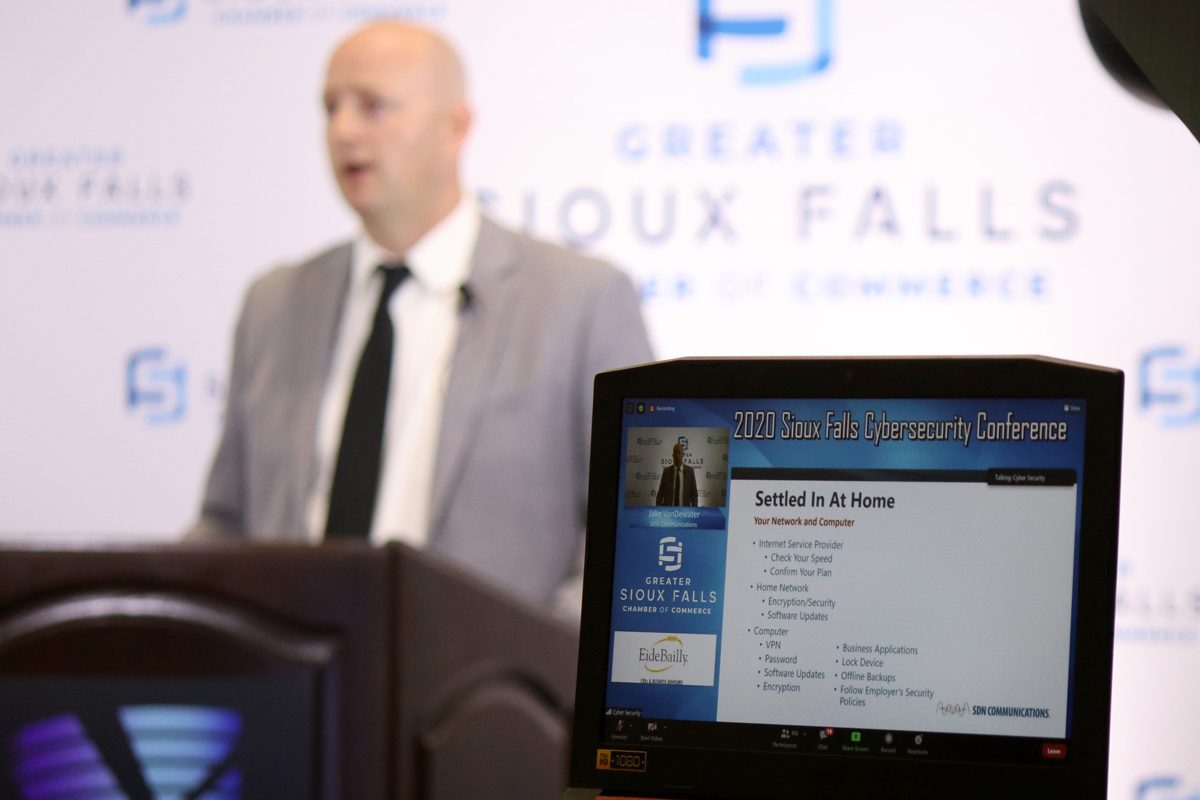
Frantz used compelling statistics like those to help explain some of the growing internet threats facing consumers, businesses and institutions. Her presentation about the “weaponization of social media” was the lead-off, keynote presentation and one of the highlights of the third annual Sioux Falls Cybersecurity Conference, which was held virtually Sept. 30.
The Greater Sioux Falls Chamber of Commerce hosted the video conference that brought more than 100 people together online.

Mary Frantz
Founder & Managing Partner
Enterprise Knowledge Partners, LLC
Frantz is the managing partner of Enterprise Knowledge Partners, LLC in the Twin Cities. The company provides cybersecurity, forensics, compliance, and technology strategy services. Her presentation made clear the need for everyone who uses social media to be more discerning and beware of possibly manipulated information.
The goal of people, groups and even nation-states that misuse technology isn’t always to modify behavior. Sometimes their objective is to steal data and other information of value.
Technology has changed, but attempts to steal information go back centuries, Frantz said.
“None of this is new. We’ve been plagiarizing methods that go back hundreds and hundreds of years,” she said.
In the 1880s, for example, attempts were made to intercept Morse code signals and hack into telegraph lines that connected continents.
Most of the presentations at the Chamber’s Cybersecurity Conference were geared toward helping businesses deal with today’s challenges.
SDN Communications, the gold sponsor of the event, provided two speakers: CEO Mark Shlanta and Jake VanDewater, the company’s vice president of engineering, operations and IT. Shlanta talked about the increasing availability of broadband technology in rural areas of South Dakota. VanDewater offered security tips for people who work remotely and the companies that employ them. (We’ll review some of VanDewater’s suggestions in a second blog about the conference.)
Among the other regional experts who spoke during the five-hour conference was Andrew Kramer, an instructor at Dakota State University in Madison. He has a passion for cybersecurity and hacks networks to help companies enhance their protective strategies.

Andrew Kramer
Computer Science Instructor
Dakota State University
Businesses don’t need a large security budget if they focus on the right areas, Kramer said. Small steps can make big differences.
Kramer identified 10 ways to keep unwanted hackers out of business networks. Here’s a summary of his suggestions:
- Passwords. Use long, complex passwords or passphrases to access accounts. Passwords should include random characters and not be predictable. If they’re strong, they don’t have to be changed as frequently.
- Account lockouts. Access to some accounts is automatically closed for a specified period of time if the wrong access credentials are used multiple times. That might delay a hacker. A more effective tactic is to give a user three unsuccessful attempts, then require the user to contact the IT staff.
- Multi-factor authentication. More than a user name and password should be required to access an account. An additional access code could be sent to the user’s cellphone, for example.
- Rate limiting. Controlling incoming or outgoing traffic can improve the flow of data and increase security. Such controls frustrate hackers.
- Network segmentation. Information from one area of a network should not be directly linked to other areas and devices. Segment Wi-Fi users from other parts of the network, for example, so that only a limited amount of information is at risk of exposure if hacked.
- Egress filtering. Most organizations routinely use firewalls to block some types of inbound traffic. Blocking outbound traffic is less common but can help trace the source of problems. This can be a big help.
- External email headers. This is a small change that can have a big impact. Label emails with a banner that notes that the message comes from outside the network. This simple action can raise alertness and help recipients identify potential problems, such as phishing emails.
- TLS certifications. Requiring digital TSL (Transport Layer Security) certification from a reputable third party is a complex process but it can significantly increase the security of wireless networks.
- BloodHound. This is a tool that outside IT experts use to graphically identify how networking equipment is connected. Company IT administrators can use the tool themselves to run tests and enhance their cybersecurity.
- Honey pots and honey tokens. These are fake accounts that contain credentials that won’t let a user access sensitive information. Honey pots or tokens are planted in a system and, if they are accessed and used, can alert a company to suspicious activity inside its network.
SDN is a leader in providing business internet, private networking and cloud connectivity to businesses and organizations in communities such as Sioux Falls, Rapid City, Worthington, and the surrounding areas.