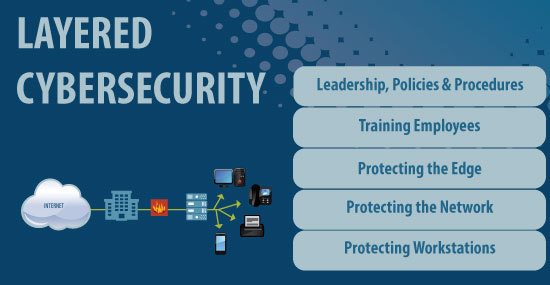
To be effective, cybersecurity should be applied in layers
The bad guys and their cyber weapons are more sophisticated than ever. They’re attacking businesses in an unrelenting style at multiple levels with increasingly advanced techniques.
To adequately protect themselves, businesses and other organizations need to take a layered approach to cybersecurity. They have to have good policies in place, maintain good security equipment at every juncture and take extra precautions with their most vulnerable asset: their employees.
“You can’t just have one layer of protection anymore,” says Vernon Brown, vice president of marketing and community relations for SDN Communications. “You can’t do it with your home. You can’t do it with your business network, either.”
As Brown notes, people use fences, locks on doors, strategically placed lighting, remotely controlled cameras, alarm systems, and other methods to protect their homes.
“Why would we treat our businesses any differently? You have to have multiple layers of protection to keep your networks safe,” he says.
The need for layered security has taken on more urgency because businesses are creating, moving and storing electronic assets of greater value than ever before. Protecting those assets is a huge responsibility that can no longer simply be the duty of a company’s IT staff or hired service.
Effective cybersecurity requires that everyone in an organization understands basic risks and how to reduce them. Employees at every level should be trained, retrained regularly and held accountable for their actions.
Layered cybersecurity has become such an important component to the success of small- and midsize businesses that Sioux Falls-based SDN is addressing the subject in a series of related website blogs and in a coming booklet. SDN is the leading regional provider of broadband connectivity and cybersecurity services for businesses and institutions. No company in the multistate service area is in a better position to break down layered security in a meaningful and understandable way.
This is the first installment in the series. It’s an introduction, a roadmap of where we’ll be taking you as we explore some of the major issues related to layered security. Other installments will focus on five key subjects:
- Executive and IT Decisions, Policies and Procedures. Establishing good, effective cybersecurity starts at the top of any organization, at the Board and CEO level or with the owner. No matter how large or small an organization is, protecting the business and its customers from cyberattacks should be a recognized priority that starts with leadership and permeates the entire company.
- Training Employees. A company’s workforce might be its most valuable asset. In most cases, employees also are the company’s most vulnerable point of access for cyberattacks. A moment of human carelessness can offset the most sophisticated security equipment. Good, ongoing training and testing of all staff members has become a necessity.
- Protecting the Edge. The point at which a company’s network connects with the outside world is an area of significant potential and great risk. Maintaining good equipment, such as up-to-date firewalls, is critically important. Services that help protect a network from attack, such as Managed DDoS Protection, also are important. We’ll point out services important to fully protecting a company’s perimeter.
- Protecting the Network. When the perimeter of a company’s network is well protected, attackers might shift more attention to an organization’s internal network. Access points such as Wi-Fi and the physical security of equipment come into play. For example, vendors and other visitors should not have wireless access to corporate data when at your business. They should be served by a separate guest network that has no access to corporate data.
- Protecting Workstations. This is a scattered target area in which poor decision-making and human error can really hurt. The basics of a good, layered security plan include having good workplace policies in place, including rules governing mobile devices. That should also include requiring strong passwords at all workstations, regularly installed antivirus updates and patches, and backing up content.
In addition to reducing vulnerabilities to attacks, deploying protective strategy at multiple levels might help detect possible breaches, measure the potential extent of damages and assess weaknesses for corrective action.
Once cybercriminals select a target, they are likely to keep hammering away until they get what they want or get frustrated and move on to another potential victim. While a single layer of protection is a start, it often isn’t enough to adequately guard a business network. A layered approach to security is the key to substantially reducing risks.
Keep reading!
The next blog in the series: Good cybersecurity must start at the top - and stay there


